Hello, welcome to the official write-up blog for the Insider Threat room!
I have no doubt that you will have fun solving this room while learning some cool information! If you're ready, let's get started.
Task 1 - Find the Threat Actor
To solve this task, we examine the log file we have. If you look closely at the file, you can see that the fmiller user first moved data into the tmp folder to bypass system permissions:
fmillers | Action/Path: Created new directory ‘/tmp/temp_export/’ on shared_drive
Here you can see that they copied many company-related files.
The main log line we need to pay attention to here is:
fmillers | Action/Path: File transfer completed from /tmp/temp_export/ to external_IP: 85.236.112.55 via SFTP. Total size: ~500MB | Event: INFO
They took the copied files and transferred them to their own server. This is definitely a crime!
Question 1 - Based on the log file, which user do you think attempted the cyberattack?
Answer: fmillers
We can find the answer to the second question in the line we need to pay attention to. "external_IP: 85.236.112.55"
Question 2 - What is the external IP address that the attacker tried to transfer data to?
Answer: 85.236.112.55
We have successfully completed this part. Now let's move on to the next part.
Task 2 - The Insider's Mistake
Let's paste the IP address we have into the given program:
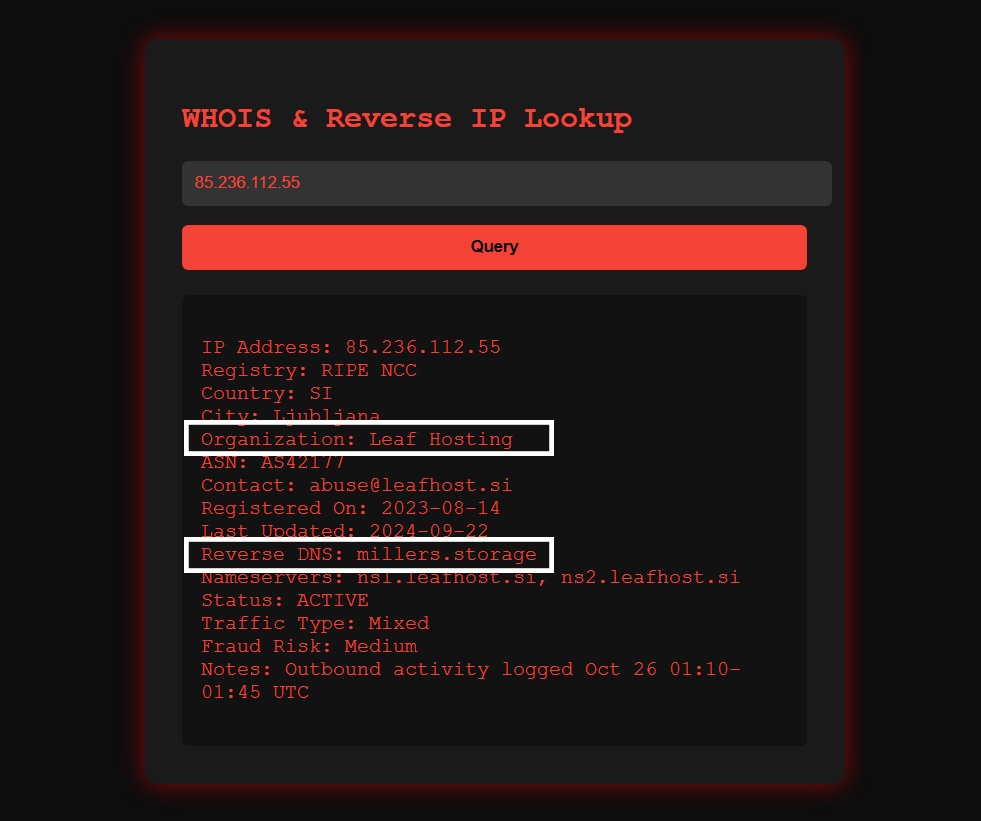
As you can see in the image, the answers to both questions are clearly visible.
Question 1 - Which company is the IP address associated with?
Answer: Leaf Hosting
Question 2 - Which DNS server appeared as a result of the reverse lookup of the IP address?
Answer: millers.storage
We can continue.
Task 3 - Location Hunt
We have an encrypted message file and an image. Let's start examining the image.
If you search for this image using reverse lookup, you will probably not get any results. Instead, it would be better to search for the prominent elements in the image. For example, let's search for the statue on the right:

Now let's focus on the statue.

Let's search for the statue using Yandex image search.
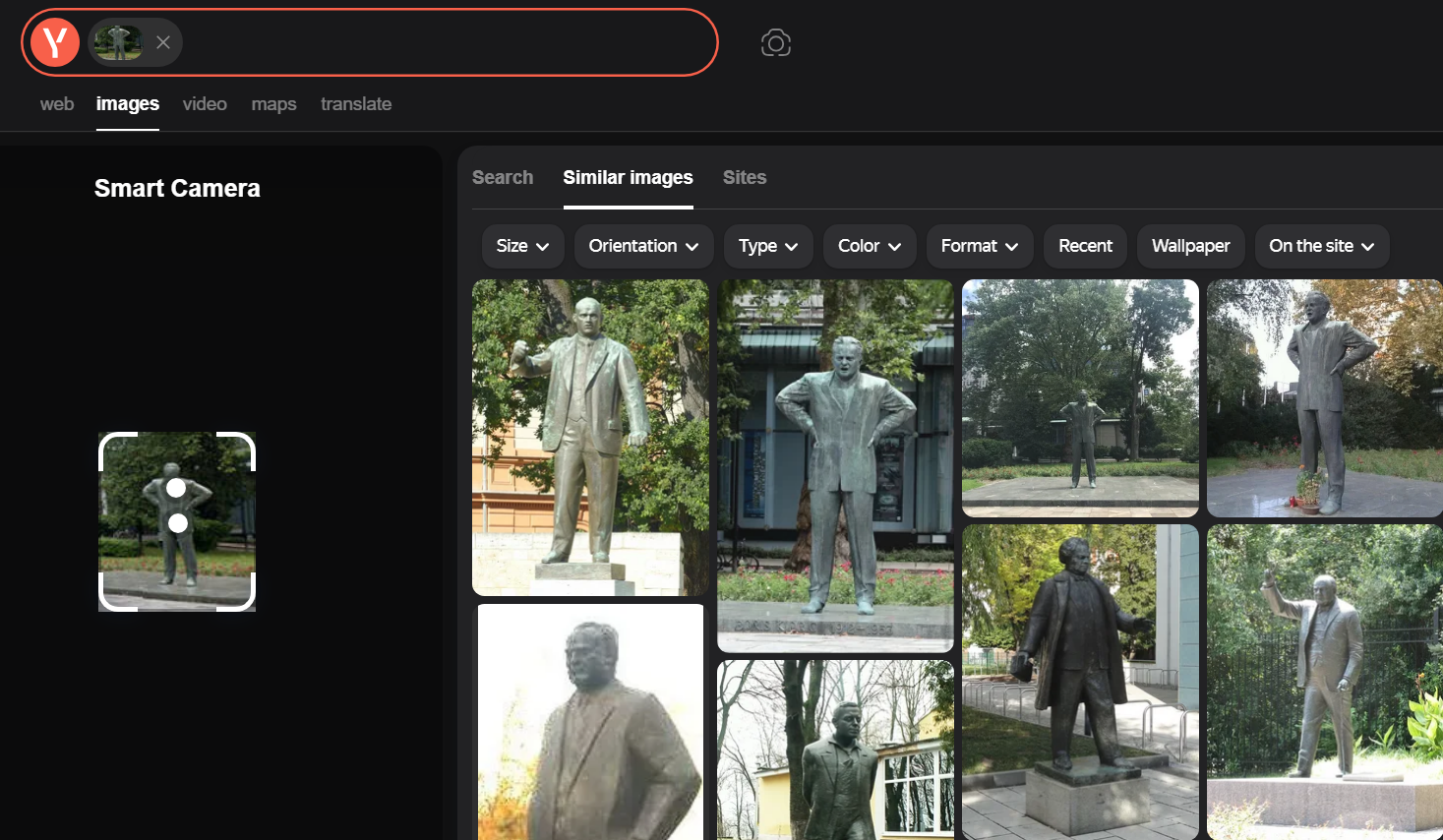
Let's click on the images.

As you can see, we have reached the location of the statue.
For those interested, the URL address of the location: maps.app.goo.gl/qgrcLtc9ed7XWDzcA
As you can see, the answer has appeared. fmillers must be in this park area right now!
Let's examine the encrypted message file.
Let's try all the key values one by one in the Caesar encryption algorithm. When we set the key value to 5, a meaningful text appears.
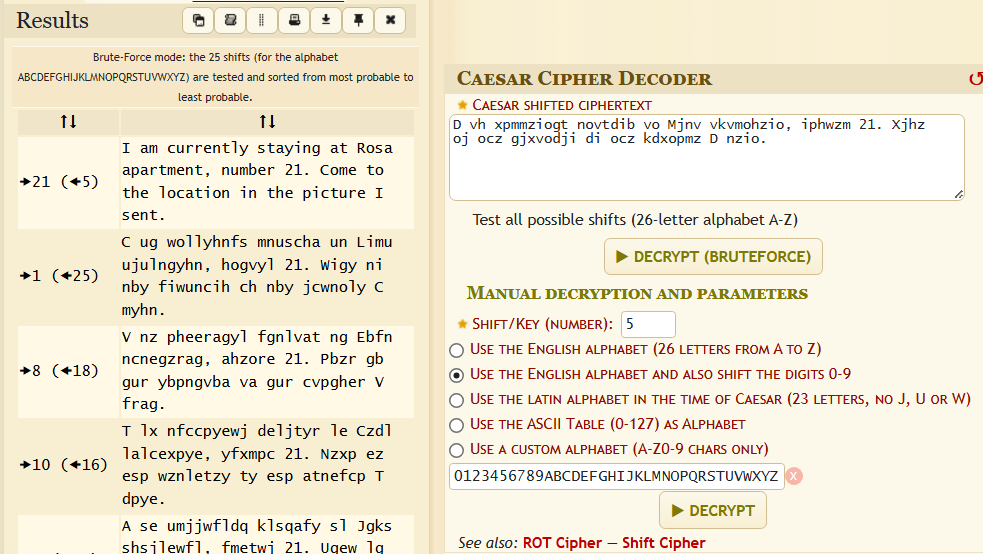
I used the dcode.fr/caesar-cipher website.
So Rosa, 21 huh! We'll be there.
Question 1 - Where was the specified image taken?
Answer: Park Sveta Evrope
Question 2 - Where does Millers live? (Apartment name, door number)
Answer: Rosa, 21
Task 4 - Station Tracking
If we look closely at the receipt found in the trash, we can see Furkan's number. Let's take this number and run our special base station scanning program.

We see Furkan's number on the receipt.
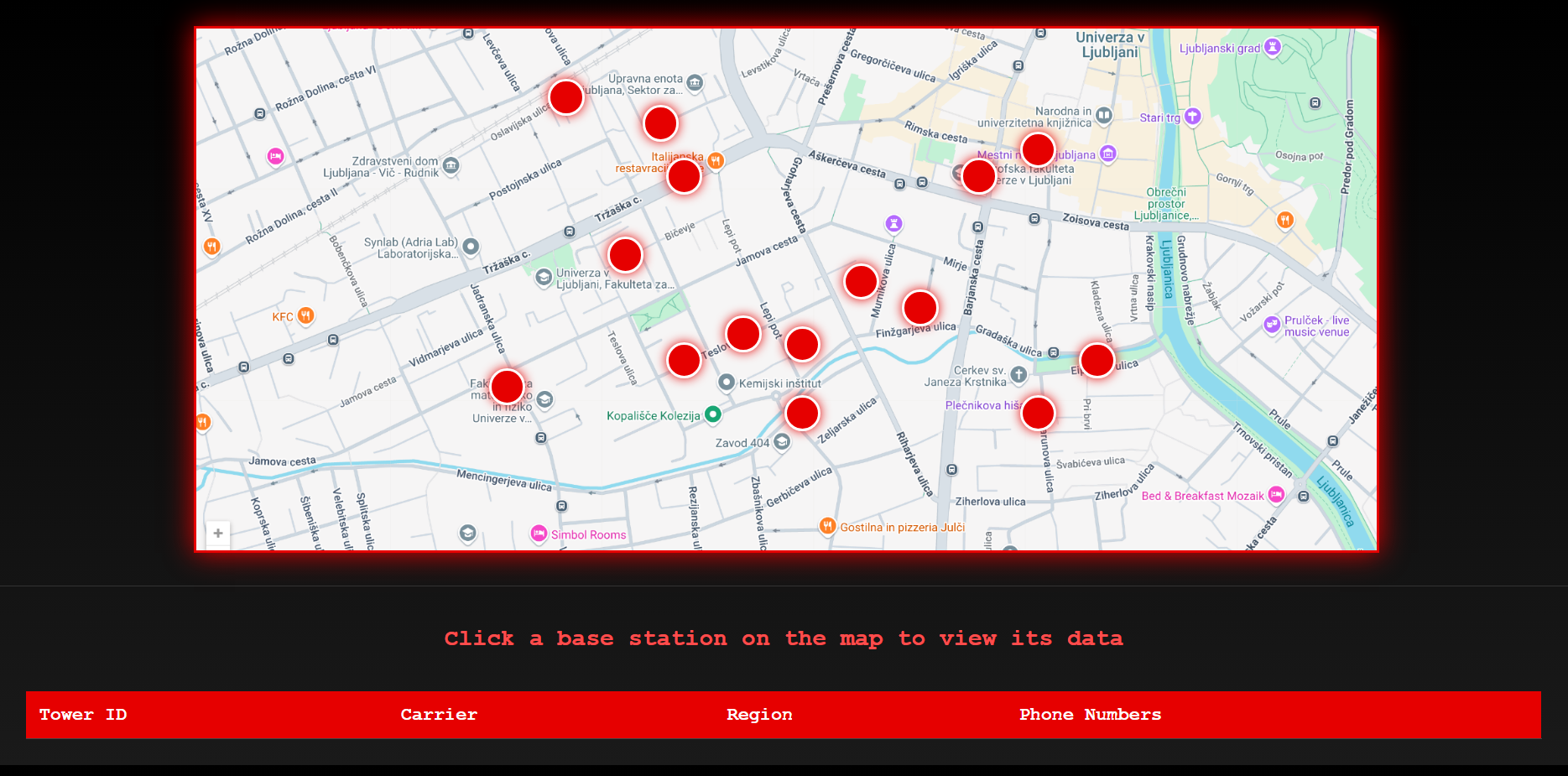
Click on each station one by one to see which one matches Furkan's number.
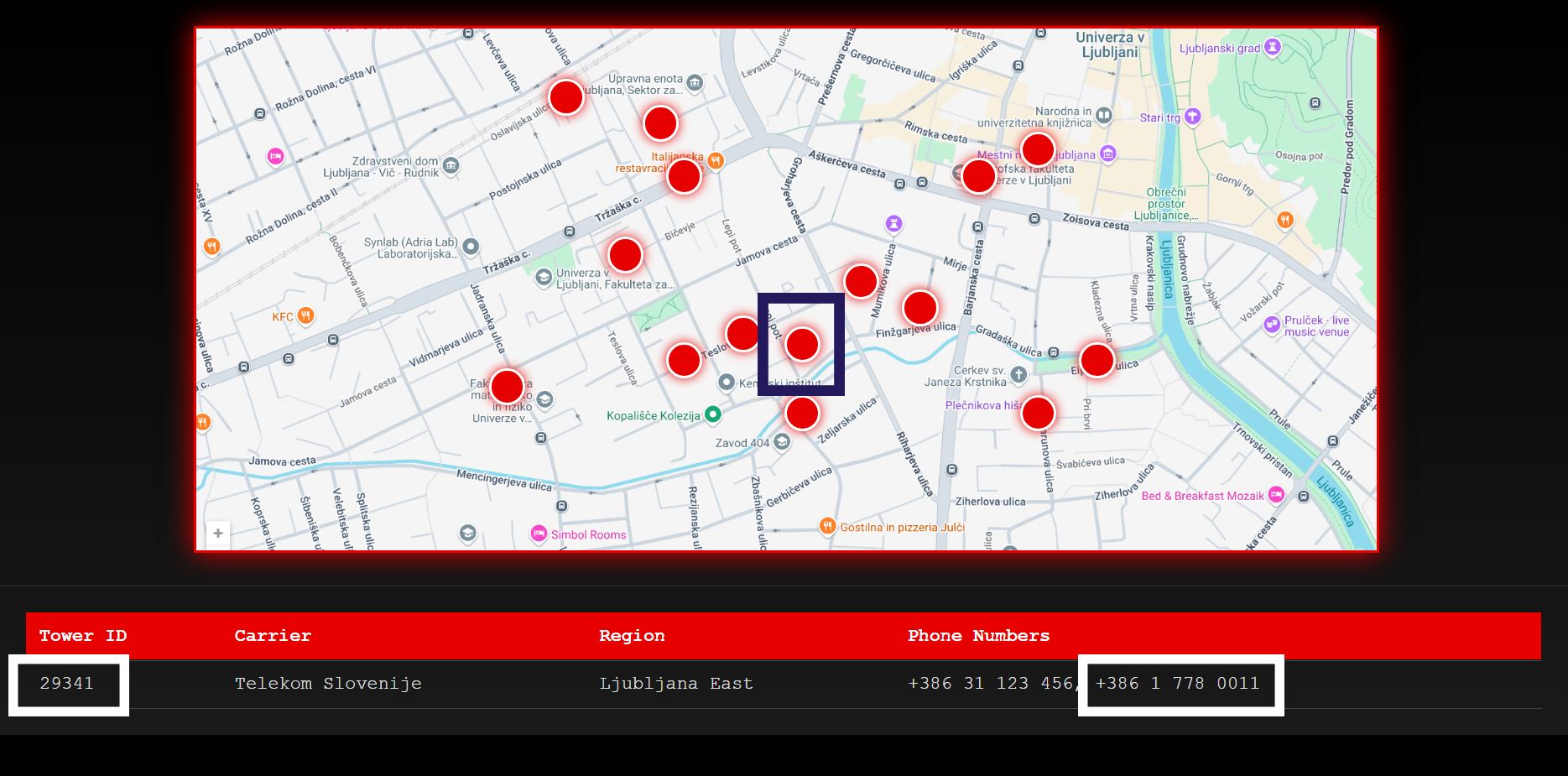
We found it! Let's immediately notify the police of this number.
Question 1 - What was the station number Millers was connected to?
Answer: 29341
Finally, our criminal apprehension operation was successful! See you in another tracking operation!